Before we dive deeper, what is a cyber attack?
Put simply, a cyber attack can be a harmful file or script developed in a way to crumble your digital resources. Some common ways a cyber attack works:
- It locks you out of your own devices.
- It holds all your files and folders hostage via encryption.
- It duplicates existing files until disks and eventually servers crash.
Now, the next important question is, how does cyber attacks and spyware penetrate organizations?
An IT infrastructure setup is like a fort with 100 doors. You have to monitor and secure all 100, but it takes just one open door to let a malicious file in. Some common entry points for a spyware or any harmful program include:
- Phishing emails
- Unauthorized access
- Social engineering
- Vulnerability exploitation
Since your team is fully trained on all security best practices, you shouldn't be worried, right?
Let's look at two examples of why you can never be too careful.
A leading transportation service provider experienced a security attack because one employee was getting tired of too many two-factor authentication authorization requests, so they approved "just one" without checking it. Consequently, the organization suffered from having multiple internal tools as well as all the employee accounts compromised for a long time after that.
The dreaded Log4j vulnerability was first reported on November 24, 2021. The first exploitation was reported on December 1, 2021, but the complete patch wasn't available until December 18, 2021. Though the vendor did a commendable job in rolling out a patch within a month, the key word to notice here is "reported." Vulnerabilities are often out in the open for a long time before being reported and fixed.
These two examples highlight why you should always be prepared for a cyber attack rather than being too trusting.
What does a cyber attack do to files?
Usually, a malicious file encrypts files so they become unreadable to the systems and the operators using them. Some harmful files may also delete, multiply, or modify the files in a server, all with the sole intention of rendering critical business and operational files useless until the organization pays the ransom.
- 01. Disk monitoring
- 02. Firewall monitoring
- 03. File monitoring
- 04. Directory monitoring
- 05. File added/deleted monitoring
- 06. File permissions monitoring
- 07. EventLog monitoring
- 08. Auto-remediation
This sounds like a cybersecurity problem. So how can Site24x7's server monitoring can help?
Site24x7's server monitoring features add an additional layer of security to your servers. In addition to monitoring the availability of your servers, the agent monitors key resources as well.
How can you use Site24x7 to add an extra layer of protection against cyber attacks?
Typically, a cyber attack tries to compromise files by:
- Disabling Windows Firewall in servers running on Windows OS
- Replicating files and folders until disks crash
- Encrypting files
- Deleting files
- Modifying files
All the above actions can be detected via Site24x7's server disk monitoring, disk partition monitoring, and resource check profiles.
Let's take a two-pronged approach to look at cyber attack indicators: top-level indicators and indicators on a more granular level.
What constitutes top-level cyber attack indicators?
Let's learn from history. How do a substantial amount of cyber attacks happen?
- A script is injected into the organization's network to disable defenses, like opening a port (5154).
- An exposed credential is abused from a remote location (4624, category 10).
- Privileges are assigned to an unauthorized account (4672).
- A brute-force attack is performed (4625 and 4670).
- Logs are cleared out (1102 and 1100).
Notice the numbers next to each anomaly? Those are the event log IDs for each type of action performed on Windows servers. The same exist for Linux servers as well, called syslogs. With Site24x7's event log monitoring, you can get alerts when a suspicious event is being performed on your servers.
How can you tackle harmful activities at a more granular level?
The answer lies with Site24x7's resource check profiles. With these profiles, you can monitor server resources, like files, directories, ports, and firewalls.
Here are some different resource check profiles Site24x7 offers:
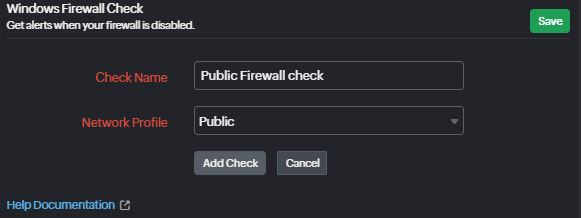
Windows Firewall check
Select the network firewall to be monitored. All three—domain, public, and private—can be monitored. This is to get an alert whenever a script or executable file disables the Windows Firewall.
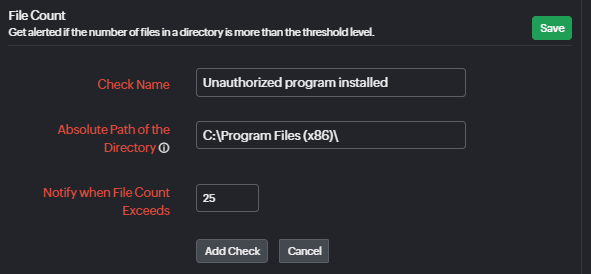
File count check
Most of the time, on Windows servers, programs are installed in C:\Program Files (x86) or C:\Program Files. It's important to know if any unauthorized program is installed in these two folders. Set a file count check on these two folders to get alerted when a new program file is installed. The same can be set for all important folders.
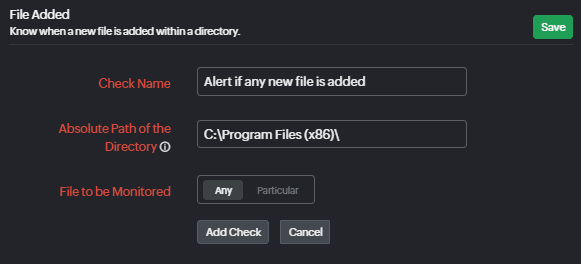
File added check
If you prefer a more stringent way to check if any file has been added to sensitive folders, you can set up a file added check and configure it to alert you if any file is added to the directory. The same alert can be set at the directory level using a subdirectory added check.
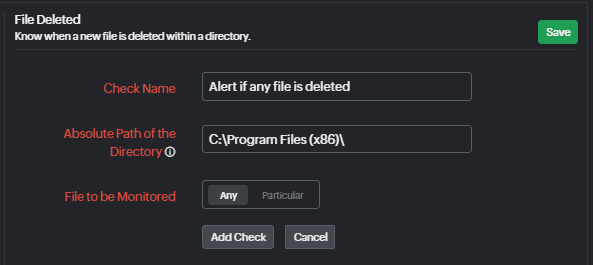
File deleted check
This check triggers an alert when a user deletes a critical file by mistake or if a malicious package does the same. You can configure this check in such a way that you get alerts if a specific file gets deleted or if any file in the directory is deleted
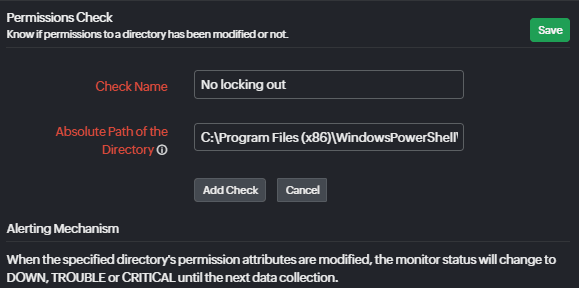
Directory permissions check
The file and directory permissions check will alert you once the permissions to a file or a directory have been changed so you can validate if the change was for good reasons, a mistake, or a byproduct of a malicious attack.
You can view the suite of checks available in our resource check profile help document. These are just a few use cases on how resource check profiles can come in handy for an organization—there are many more ways resource checks can help.
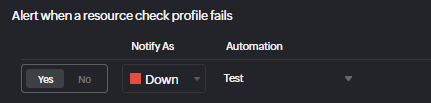
But is that all Site24x7 offers when files are compromised?
With Site24x7's server monitoring, you get detection and auto-remediation capabilities as well. What could be the remediation action when a directory is filling the entire disk without any limits? Since there will be backups, the first course of action is to delete the contents of the directory and restore it with a backup. But what if the directory is attacked in the middle of the night? Site24x7's server monitoring agent can invoke automatic remediation actions, like running a script, command, or reboot action when resource checks trigger a warning alert. This can be done in the threshold profile of the server.
Why should you choose Site24x7's server monitoring?
ManageEngine Site24x7 is an observability platform for your entire IT infrastructure. Site24x7 kicks into action when the first performance degradation is detected and before it snowballs into an outage. With Site24x7, an enterprise-grade, AI-driven, robust, and reliable monitoring platform is watching over your IT infrastructure every second of the day.

What sets Site24x7 apart from the competition?
To help you decide if Site24x7 is the tool for your needs, we'll let you hear from our customers—this is what they had to say when we asked them what they loved the most:
Observability in one browser tab
With Site24x7, you can monitor servers, databases, Kubernetes, all three major public clouds (Azure, GCP, and AWS), websites, and applications.
No-surprises billing
Even when you have an auto-scaling containerization setup, cloud infrastructure, or log ingestion, you will always know how much you will pay for monitoring.
Zero-touch integrations
All services, processes, databases, cloud resources, and applications are auto-discovered. You don't have to manually add anything for monitoring unless you want to.
You can try our zero-restrictions server monitoring trial here. Or, our support team will gladly assist you if you would like a personalized demo tailored to your requirements.